Understanding Phishing Emails
Phishing emails, a prevalent online scam, are fraudulent messages disguised as legitimate communications to steal personal information. Often posing as trustworthy entities, these emails aim to deceive individuals into revealing sensitive data like passwords or credit card details. Their implications can be severe, leading to financial losses or identity theft.
The threat of phishing scams is growing rapidly, with cybercriminals frequently updating their tactics to evade detection. As technology evolves, so do the methods used by these malicious actors, making it crucial for individuals and businesses to stay informed.
In the same genre : Exploring the revolutionary world of unmanned aerial vehicles with continuous power
Recognizing phishing attempts is vital for maintaining personal security. Awareness of such scams empowers individuals to protect themselves against potential threats. By understanding the characteristics of phishing emails, users can avoid falling victim to these deceptive tactics.
The importance of identifying phishing email signs cannot be overstated. From unusual sender addresses to mismatched URLs, spotting these red flags can prevent users from unwittingly compromising their personal information. Consequently, fostering a culture of vigilance and caution when dealing with online scams is indispensable for safeguarding personal and organizational security.
Also to see : Enhance your home wi-fi: boost speed and ensure reliable connectivity
Key Indicators of Phishing Emails
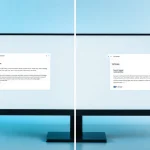
Phishing emails often exhibit specific visual clues that can alert you to their deceitful nature. Firstly, examine the sender’s email address carefully. Unusual sender addresses are a common sign that the email may not be legitimate. Attackers often use email addresses that slightly mimic a trusted source, hoping recipients won’t notice the difference. Additionally, look for generic greetings, such as “Dear Customer,” rather than personalized messages. Such impersonal salutations hint at a bulk phishing attempt rather than a genuine communication.
Another critical email red flag is mismatched URLs. Hover over any links within the email (without clicking) to view the actual destination URL. If it doesn’t match the displayed hyperlink or connect to a legitimate site, you’re likely looking at a phishing attempt. The deceptive tactics employed often extend to the domain used for the email address. Phishers might use domains that closely resemble legitimate ones, often changing a letter or two.
By recognizing these signs of phishing, you can better protect yourself from falling victim to online scams. Remaining vigilant and questioning suspicious emails is key to maintaining robust email security.
Deceptive Tactics Used by Attackers
Phishing scams rely heavily on social engineering to deceive their victims. By manipulating people’s trust, attackers exploit psychological triggers to coerce individuals into revealing sensitive information. Social engineering techniques often involve crafting emails that mimic genuine communications, using familiar logos and branding to mislead users. Such emails might appear to be from reputable companies or institutions, borrowing their logos, styles, and colours, making the deception even more convincing.
Attackers frequently leverage urgency and fear in their phishing attempts. For example, an email might claim your bank account has been compromised, urging immediate action to resolve the issue. By inciting panic, phishers push recipients to respond hastily without scrutinizing the authenticity of the message. This method is not only about urgency but also a play on the recipient’s anxiety over potential loss or harm.
Common malicious techniques also involve creating a scenario of impending doom to prompt immediate response, like subscription cancellations or unauthorized transactions. Such strategies prey on the fear of inconvenient consequences, convincing victims to comply with the attackers’ demands swiftly, often at the cost of their personal information.
Examples of Real Phishing Emails
Understanding real-world phishing email examples can significantly aid in recognizing and avoiding these threats. By examining case studies, individuals can learn to identify common red flags and deceptive tactics used by phishers in their attempts to steal sensitive information.
Case Study: Banking Scams
A prevalent example is a phishing email disguised as a communication from a bank. These emails often mimic legitimate bank emails, using logos and branding to appear authentic. Common signs include a generic greeting like “Dear Valued Customer” and a sense of urgency, such as a warning about a compromised account. Visual clues, such as mismatched URLs, often reveal their fraudulent nature. Detecting these red flags is critical to preventing personal information theft.
Case Study: Tech Support Scams
Another tactic involves tech support scams, which lure victims with claims of critical issues affecting their devices. Phishers typically impersonate reputable tech companies, pressuring users to provide remote access or purchase unnecessary software. By employing fear and distrust, these scams effectively manipulate recipients into quick action without verification.
By analyzing these real threats, individuals can better identify the tactics employed and protect themselves against falling victim to such phishing email examples.
Practical Tips for Verifying Email Authenticity
Email verification is essential in safeguarding against phishing attacks. Before clicking on links or downloading attachments, take time to scrutinize the email. Confirm the sender’s identity by checking the email address and double-check its domain. Look for subtle inconsistencies, such as misplaced letters or numbers, that could signify a spoofed domain.
Employ security measures like installing reliable email filters. These tools automatically detect and quarantine suspicious emails, reducing exposure to potential threats. Keeping software updated also bolsters your defenses against ever-evolving phishing tactics.
Utilize tools and resources for further verification. Services like DMARC or DKIM ensure email authenticity by validating sender addresses. These protocols add extra layers of protection against spoofing attempts. If an email raises suspicion, consider using online resources to verify its legitimacy before engaging further.
Finally, never underestimate the role of reputable security software. An up-to-date antivirus program can identify malicious attachments and shield against unauthorized access, providing comprehensive protection. By adopting these practices, you enhance your email security and diminish the risk of falling victim to online scams.
Reporting Phishing Attempts
Understanding how to report phishing attempts is crucial in combating this prevalent threat and enhancing cybersecurity. By reporting these malicious efforts, you not only protect yourself but also help prevent others from falling victim.
How to Report Phishing Emails
Starting with the procedure for reporting phishing emails, contact your email provider directly. Most providers have a dedicated function for flagging suspicious messages, which enables them to take swift action. Moreover, reaching out to relevant authorities or companies involved in the phishing scam can lead to more effective countermeasures.
Sharing Awareness with Others
Raising community awareness is equally important. Share your knowledge about phishing protection openly, encouraging others to stay informed. This collective vigilance strengthens the overall defence against these scams.
Resources for Ongoing Learning
Finally, leverage a wealth of resources from websites and organizations devoted to cybersecurity education. Keeping abreast of the latest phishing threats and strategies ensures you’re well-prepared. Follow updates and continuously expand your knowledge to safeguard against evolving tactics. Together, these efforts can make a significant impact in defending against online scams.